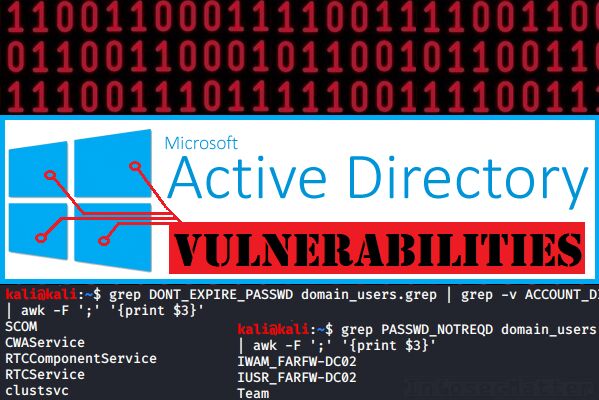
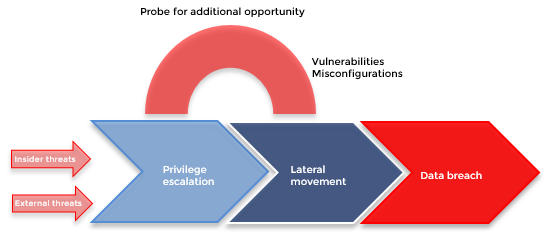
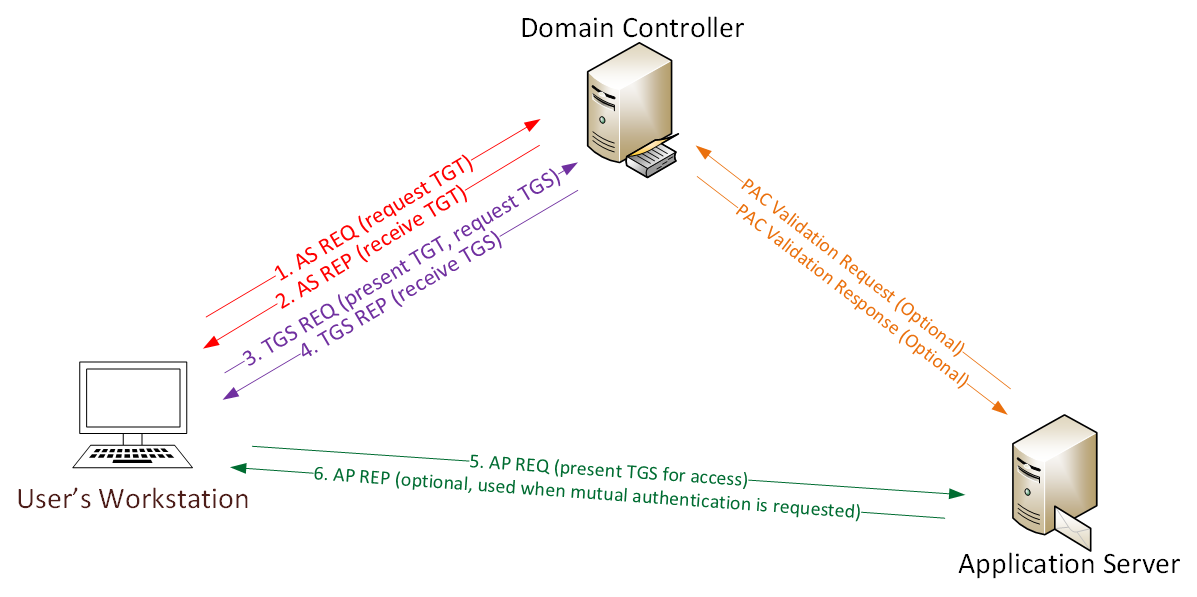
Pentester Academy on Twitter: "Understand and practice the basics of attacking Active Directory using metasploit and other tools in our Attacking Active Directory with Linux lab. #LinuxAD https://t.co/nEuJFib30U https://t.co/PRGQlnsuqU" / X
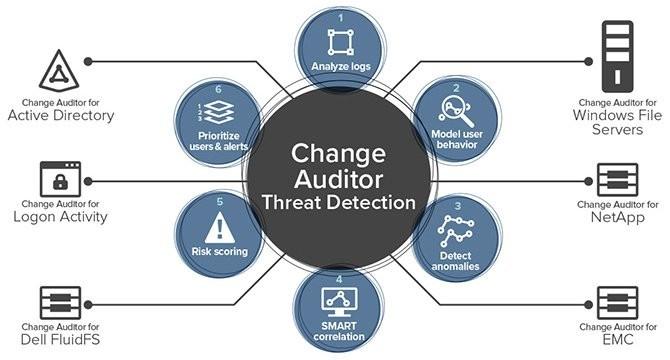
Active Directory's Attack Surface is Huge – Here's How to Find a Threat Needle in its Log Haystack | DLT Solutions, a Tech Data company